Convert The Sha 256 Private Key images are ready in this website. Convert The Sha 256 Private Key are a topic that is being searched for and liked by netizens now. You can Get the Convert The Sha 256 Private Key files here. Find and Download all royalty-free photos and vectors.
If you’re looking for Convert The Sha 256 Private Key images information connected with to the Convert The Sha 256 Private Key interest, you have visit the ideal site. Our website always provides you with suggestions for seeking the maximum quality video and image content, please kindly surf and locate more informative video articles and graphics that fit your interests.
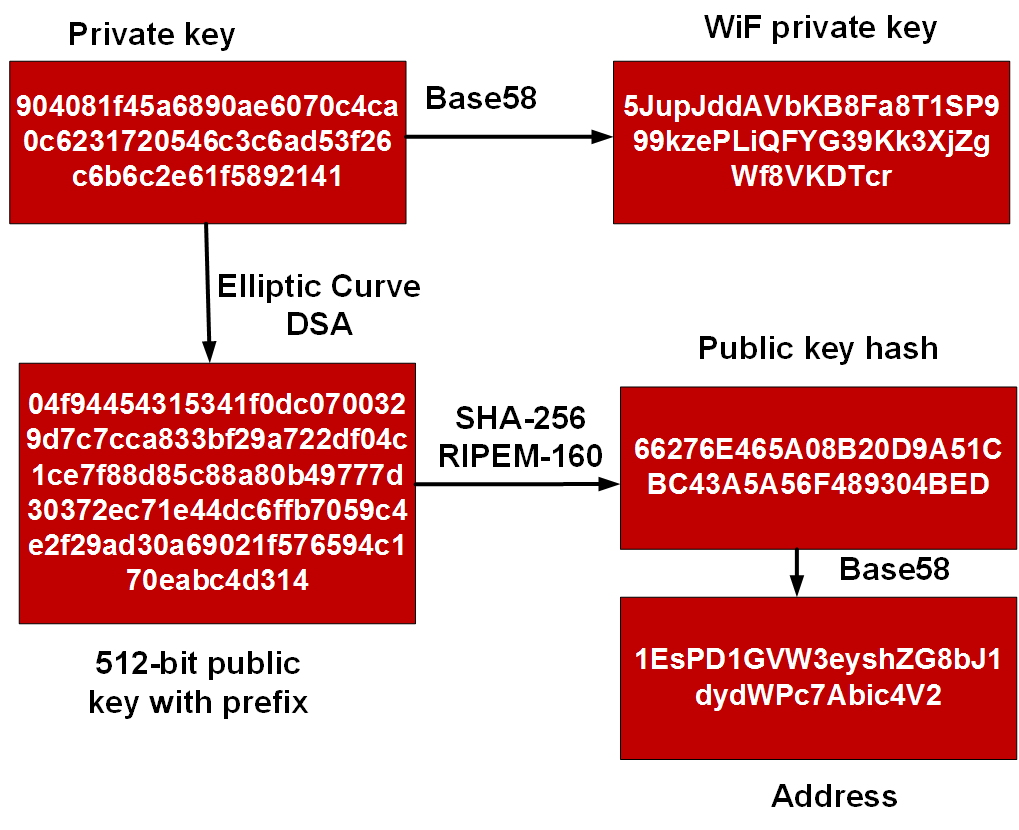
Convert The Sha 256 Private Key. This is the checksum. The wallet key generation process can be split into four steps. When generating the SHA-256 private key the chip returns me the public key. Depending on the form of public key full or compressed we get different addresses but both are perfectly valid.

 39 99 15 Off Sticky Password Premium Lifetime Subscription 2019 Checkout Now Have You Ever Face To The Lost Password Situati Sticky Subscription Passwords From pinterest.com
39 99 15 Off Sticky Password Premium Lifetime Subscription 2019 Checkout Now Have You Ever Face To The Lost Password Situati Sticky Subscription Passwords From pinterest.com
We have explained the SHA or Secure Hash Algorithm in our older article. 1 - Private key. P7B certificates contain —–BEGIN PKCS7—– and —–END PKCS7—– statements. Encoding the key with Base58. 3 - SHA-256 hash of 2. Creating a public key with ECDSA.
Calculating the checksum with double SHA-256.
Encoding the key with Base58. Perform a SHA-256 hash on the extended key. 7 - Base58 encoding of 6. If you would like to try to replicate these steps these private keys are not obfuscated like my other blogs the private. Take a private key. HMACHash-based message authentication code is a message authentication code that uses a cryptographic hash function such as SHA-256 SHA-512 and a secret key known as a cryptographic key.

 Source: in.pinterest.com
Source: in.pinterest.com
2 - Add 0x80 byte to the front. Privatepublic keys SHA-256 keys SHA-256 is a hash algorithm. 7 - Base58 encoding of 6. When generating the SHA-256 private key the chip returns me the public key. The wallet key generation process can be split into four steps.
 Source: pinterest.com
Source: pinterest.com
Here is how to generate CSR Private Key with SHA256 signature with OpenSSL for either reissue or new request to get SSLTLS Certificate. 5 - First 4 bytes of 4 this is the checksum. Take the first four bytes of the second SHA-256 hash. Privatepublic keys SHA-256 keys SHA-256 is a hash algorithm. The need to throw a complete new guide to Generate CSR Private Key With SHA256 Signature is to correct our existing older guides on Generating CSR as almost all the browsers will throw.
 Source: medium.com
Source: medium.com
However it returns me not a public key in a pem format but according to the datasheet it returns me the coordinates X and Y of the public key which are 64 bytes. 4 - SHA-256 hash of 3. Creating a public key with ECDSA. Depending on the form of public key full or compressed we get different addresses but both are perfectly valid. Calculating the checksum with double SHA-256.
 Source: medium.com
Source: medium.com
The PKCS7 or P7B format is usually stored in Base64 ASCII format and has a file extension of p7b or p7c. Generate a SHA-256 hash with this free online encryption tool. In fact each private key controls at least four different public addresses as demonstrated below. 5 - First 4 bytes of 4 this is the checksum. 4 - SHA-256 hash of 3.
 Source: in.pinterest.com
Source: in.pinterest.com
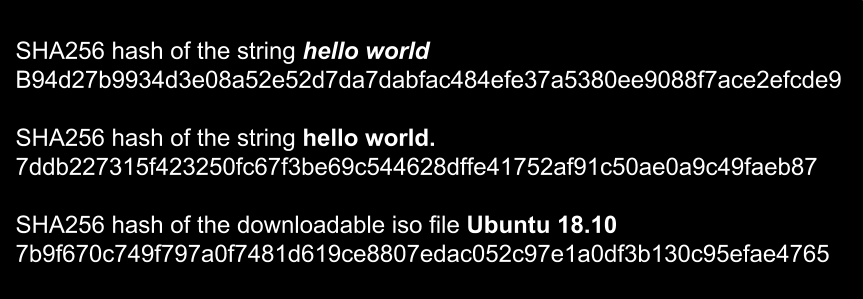
Generate the SHA256 hash of any string. Calculating the checksum with double SHA-256. HMACHash-based message authentication code is a message authentication code that uses a cryptographic hash function such as SHA-256 SHA-512 and a secret key known as a cryptographic key. For correct checksum results make sure to set the SHA-256 hash input for hexadecimal data not ASCII text. If you would like to try to replicate these steps these private keys are not obfuscated like my other blogs the private.
 Source: in.pinterest.com
Source: in.pinterest.com
The two additional addresses are the P2WPKH-P2SH public addresses that begin with 3 and native Segwit P2WPKH addresses also called Bech32 addresses public addresses that begin with bc1. 2 - Add 0x80 byte to the front. Generate the SHA256 hash of any string. HMAC is more secure than any other authentication codes as it contains Hashing as well as MAC. 6 - Adding 5 at the end of 2.
 Source: pinterest.com
Source: pinterest.com
In fact each private key controls at least four different public addresses as demonstrated below. We have explained the SHA or Secure Hash Algorithm in our older article. Take a private key. 6 - Adding 5 at the end of 2. For correct checksum results make sure to set the SHA-256 hash input for hexadecimal data not ASCII text.
 Source: devglan.com
Source: devglan.com
This online tool allows you to generate the SHA256 hash of any string. Perform a SHA-256 hash on result of SHA-256 hash. Encrypting the key with SHA-256 and RIPEMD-160. To further enhance the security of you encrypted hash you can use a shared key. A P7B file only contains certificates and.
 Source: bitcoin.stackexchange.com
Source: bitcoin.stackexchange.com
A P7B file only contains certificates and. A P7B file only contains certificates and. Generate the SHA256 hash of any string. Append a 0x01 byte after it if it should be used with compressed public keys. Add a 0x80 byte in front of it for mainnet addresses.
 Source: devglan.com
Source: devglan.com
HMAC is more secure than any other authentication codes as it contains Hashing as well as MAC. However it returns me not a public key in a pem format but according to the datasheet it returns me the coordinates X and Y of the public key which are 64 bytes. However it returns me not a public key in a pem format but according to the datasheet it returns me the coordinates X and Y of the public key which are 64 bytes. P7B certificates contain —–BEGIN PKCS7—– and —–END PKCS7—– statements. Generate a SHA-256 hash with this free online encryption tool.
 Source: ikomodo.com
Source: ikomodo.com
This online tool allows you to generate the SHA256 hash of any string. Encrypting the key with SHA-256 and RIPEMD-160. This is the checksum. Creating a public key with ECDSA. Encoding the key with Base58.

This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site value, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title Convert The Sha 256 Private Key by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.





